MikroTik CHR: How to set up OpenVPN server for your IoT devices (+ video)
In this article, we will show you how to configure an OpenVPN server in your MikroTik Cloud Hosted Router using WinBox and RouterOS CLI.
IMPORTANT: The date on the router must be within the range of the installed certificates valid period. To prevent certificate verification issues, enable NTP synchronization on both the server and the client.
Here’s a small video explaining the process:
1. Updating RouterOS to the latest stable version
You can skip this if your router is already up to date. Make sure you have a backup of your configuration before proceeding.
To update your router, go to System>Packages and click on “Check for updates”,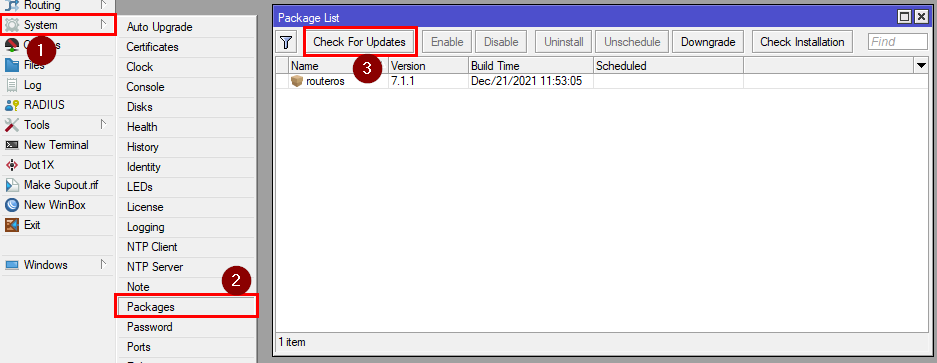
If your MikroTik router is not updated, you will be presented with the new version and a changelog for it. Click on "Download and Install" or "Download", if you plan to reboot and apply the update later. After it’s downloaded, your router will reboot to apply the update.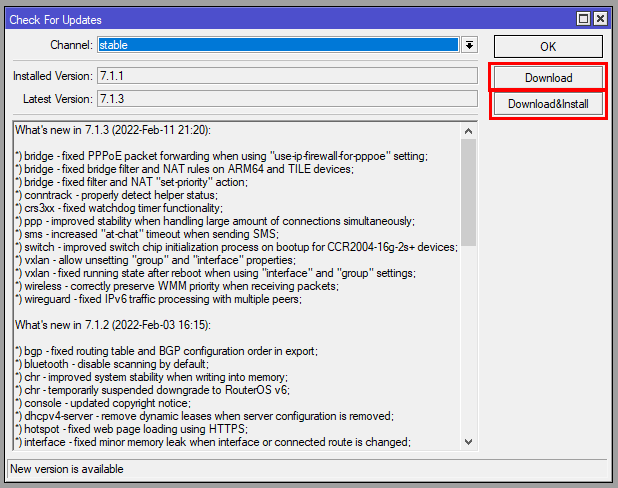
In this article, we will use 192.168.34.0/24 as our OpenVPN Network.
2. Creating a bridge for the OpenVPN network
Go to Bridge and click on "+". Name the bridge as you like(e.g. OVPN-Bridge) and click on "OK".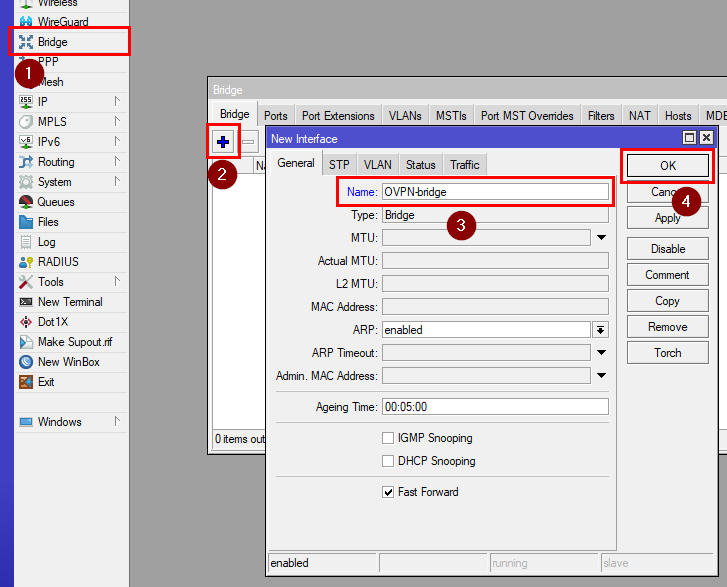
Alternatively, you can create a bridge through "Interfaces". After clicking on "+" select bridge.
RouterOS CLI Command:
[admin@MikroTik] > interface bridge add name=OVPN-bridge
3. Setting an IP address for your VPN Network
Go to IP>Addresses and click on "+". Set 192.168.34.1/24 as the аddress and select the new bridge you’ve created(in our case OVPN-Bridge).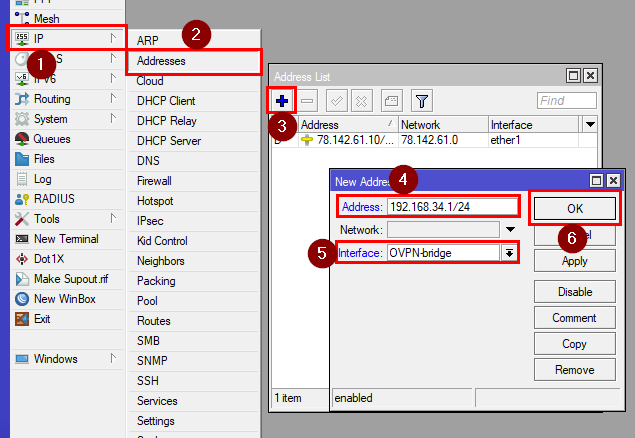
RouterOS CLI Command:
[admin@MikroTik] > ip address add address=192.168.34.1/24 interface=OVPN-bridge
4. Creating an IP pool for your OpenVPN network
Go to IP>Pools and click on "+". Set the range to 192.168.34.100-192.168.34.200 and name the pool as you like(e.g. OVPN-pool).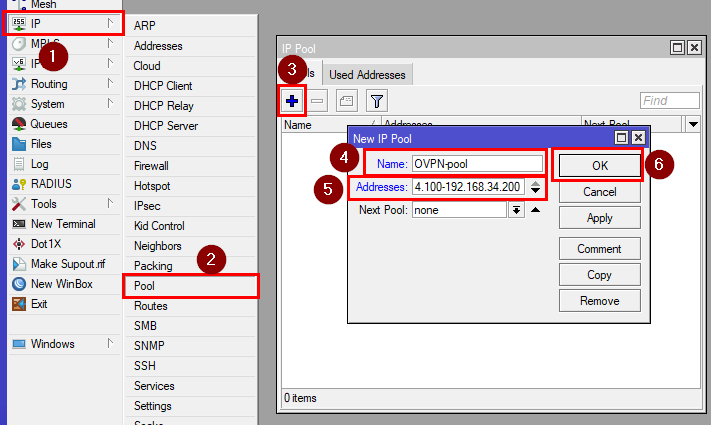
RouterOS CLI Command:
[admin@MikroTik] > ip pool add name=OVPN-pool ranges=192.168.34.100-192.168.34.200
5. Creating a firewall filter rule
Go to IP>Firewall and create a new rule with these settings:
Chain: input
Protocol: TCP
Dst. Port: 1194(or 443)
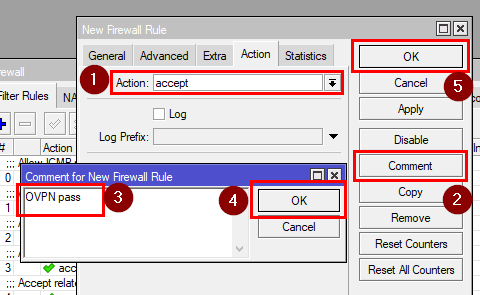
Action: accept
Comment: OVPN pass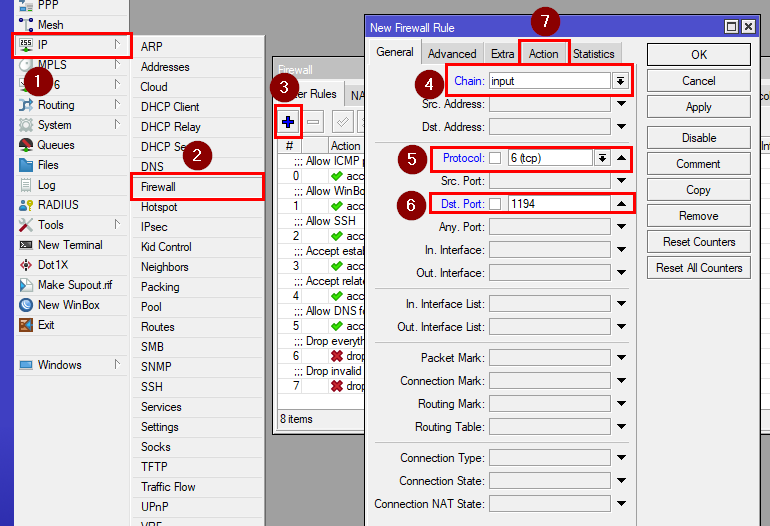
Then move the rule to higher priority by dragging it above drop rules.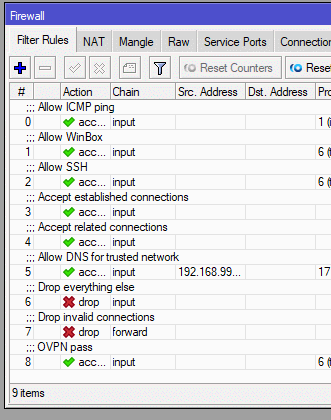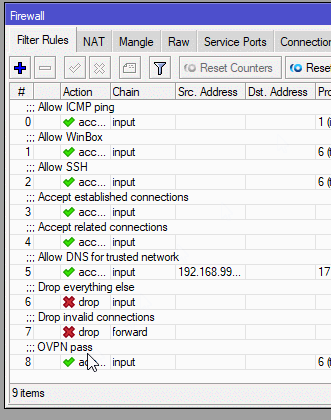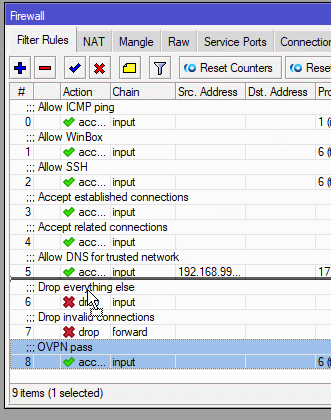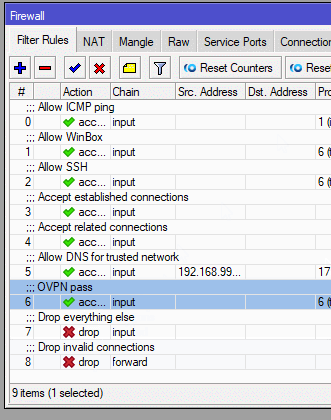
In RouterOS CLI you need to list all the rules, you can do that by using this command:
[admin@MikroTik] > ip firewall filter print all without-paging
It should output something like this:
0 ;;; Allow ICMP ping
chain=input action=accept protocol=icmp
1 ;;; Allow WinBox
chain=input action=accept protocol=tcp dst-port=8291
2 ;;; Allow SSH
chain=input action=accept protocol=tcp dst-port=22221
3 ;;; Accept established connections
chain=input action=accept connection-state=established
4 ;;; Accept related connections
chain=input action=accept connection-state=related
5 ;;; Allow DNS for trusted network
chain=input action=accept protocol=udp src-address=192.168.99.0/24
dst-port=53
6 ;;; Drop everything else
chain=input action=drop
7 ;;; Drop invalid connections
chain=forward action=drop connection-state=invalid
Enter these two commands, where X is the number of the first drop rule:
[admin@MikroTik] > ip firewall filter add chain=input action=accept comment="OVPN pass" protocol=tcp dst-port=1194 place-before=X
In the end, it should look like this:
...
5 ;;; Allow DNS for trusted network
chain=input action=accept protocol=udp src-address=192.168.99.0/24
dst-port=53
6 ;;; OVPN pass
chain=input action=accept protocol=tcp dst-port=1194
7 ;;; Drop everything else
chain=input action=drop
...
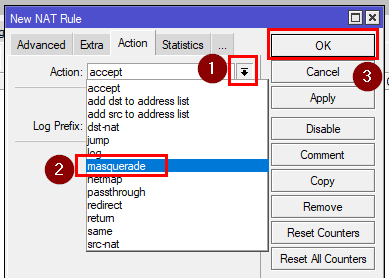
6. Enabling the NAT for the OpenVPN
Go to the NAT tab and click on "+".
Input: srcnat
Out. Interface: ether1
Action: masquerade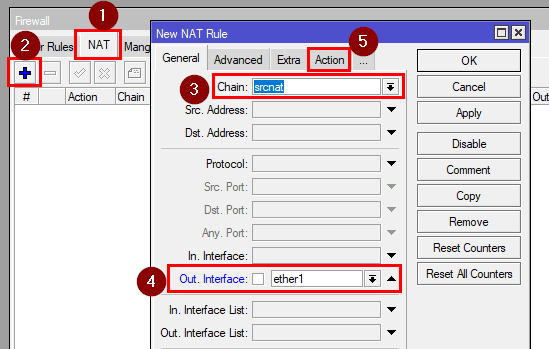
RouterOS CLI Command:
[admin@MikroTik] > ip firewall nat add chain=srcnat out-interface=ether1 action=masquerade
7. Making and signing the certificates
In this article, we will create and use self-signed ones.
Go to System > certificates and click on "+".
7a. Creating and signing the Certificate Authority
You can name it as you like, in our example, we will name it LMTCA(Local MikroTik Certificate Authority). Enter:
Name: LMTCA
Your Location/Organization data
Common Name: LMTCA
Key size: 4096
Days valid: e.g. 3650
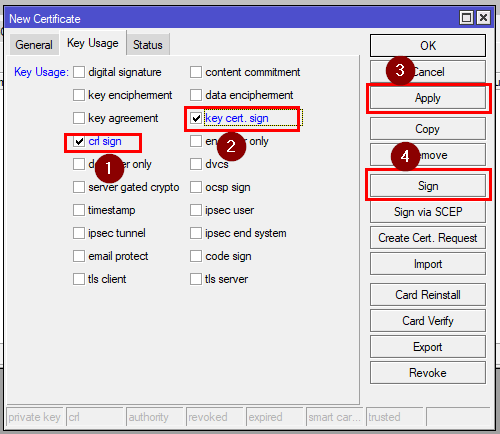
Then go to the Key Usage tab and select only crl sign and key cert sign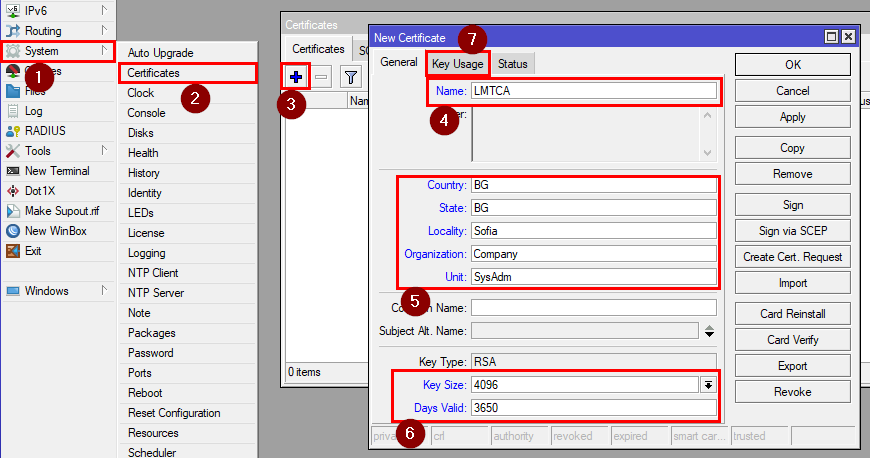
RouterOS CLI Command:
[admin@MikroTik] > /certificate add name=LMTCA country="BG" state="BG" locality="Sofia" organization="Company" unit="SysAdm" common-name="LMTCA" key-size=4096 days-valid=3650 key-usage=crl-sign,key-cert-sign
Now save the certificate and sign it with CRL host set to the public IP of your MikroTik CHR.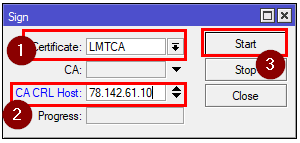
RouterOS CLI Command:
[admin@MikroTik] > /certificate sign LMTCA ca-crl-host=YourMCHRPublicIP
7b. Creating and signing the OpenVPN Server Certificate
Name: SERVER
Your Location/Organization data
Common Name: Your public IP of your MikroTik CHR
Key size: 4096
Days valid: e.g. 3650
Then go to the Key Usage tab and select only digital signature, key encipherment, and tls server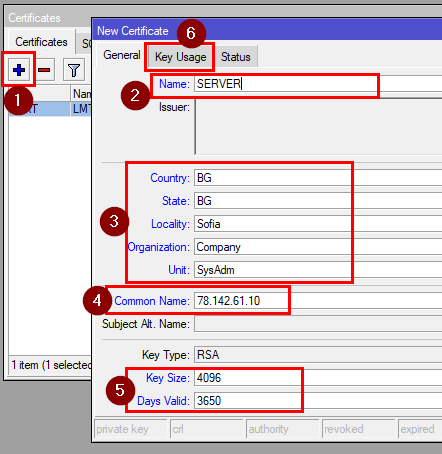
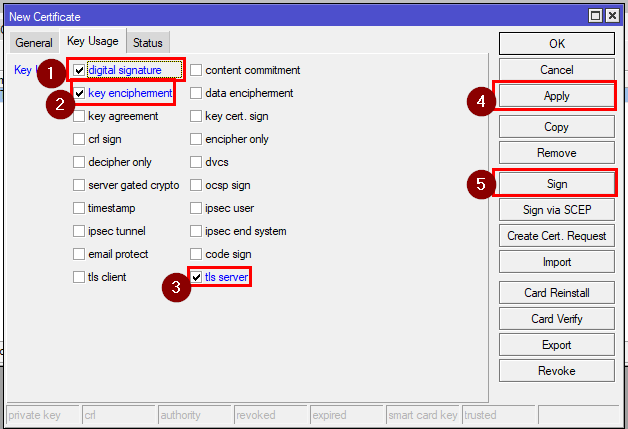
RouterOS CLI Command:
[admin@MikroTik] > /certificate add name=SERVER country="BG" state="BG" locality="Sofia" organization="Company" unit="SysAdm" common-name="YourMCHRPublicIP" key-size=4096 days-valid=3650 key-usage=digital-signature,key-encipherment,tls-server
Now save the certificate and sign it with the newly created CA. 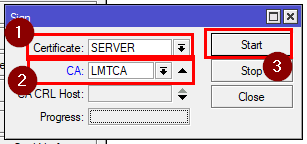
After that, go to the General tab(or double-click the server certificate if you closed it) and mark "Trusted"
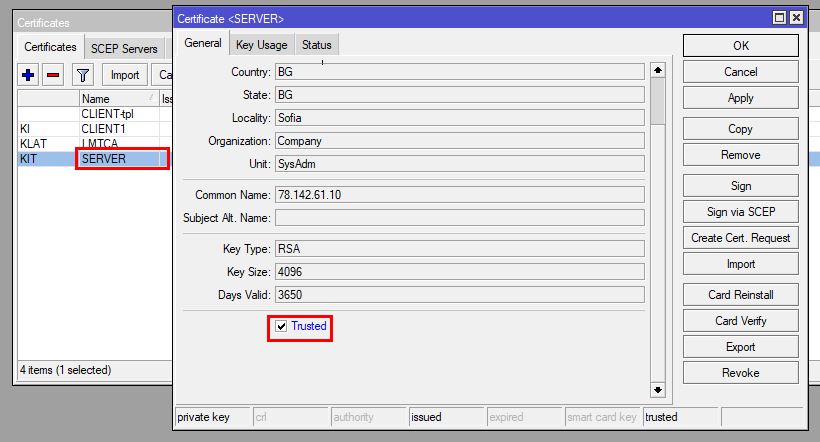
RouterOS CLI Command:
[admin@MikroTik] > /certificate sign SERVER ca="LMTCA"
[admin@MikroTik] > /certificate set SERVER trusted=yes
7c. Creating a template and making the Client certificates from it
Name: CLIENT-tpl
Your Location/Organization data
Common Name: CLIENT
Key size: 4096
Days valid: e.g. 3650
Then go to the Key Usage tab and select only tls-client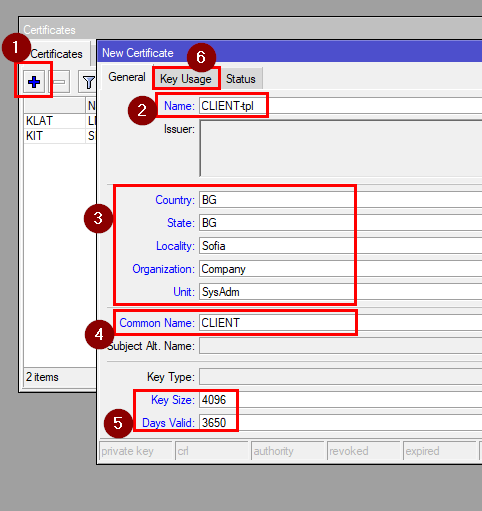
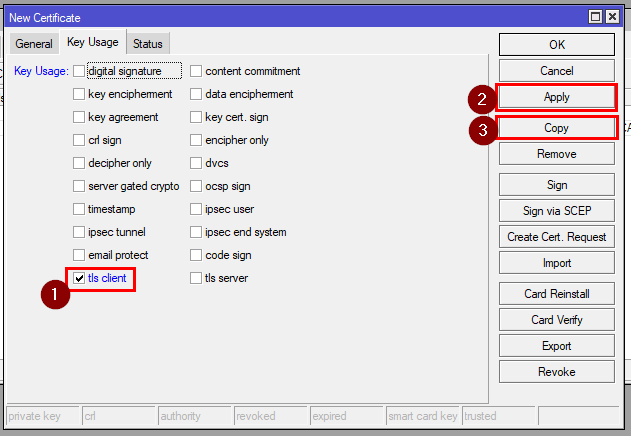
RouterOS CLI Command:
[admin@MikroTik] > /certificate add name=CLIENT-tpl country="BG" state="BG" locality="Sofia" organization="Company" unit="SysAdm" common-name="CLIENT" key-size=4096 days-valid=3650 key-usage=tls-client
Save it. From this template, we will be making the certificates for the clients. This is done by clicking on “Copy”.
Now rename both the name and common name to CLIENT1 (for other clients you can name them CLIENT2, CLIENT3, etc.)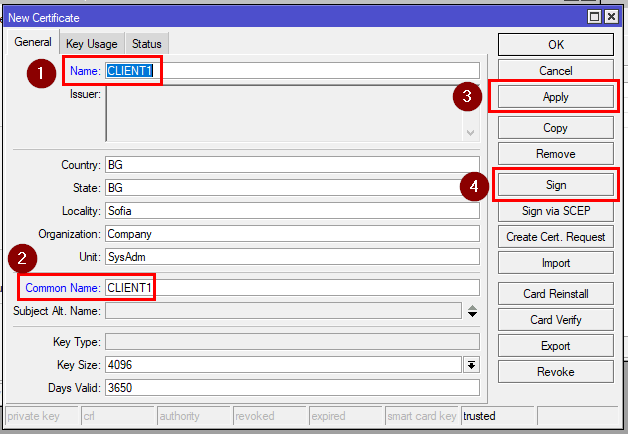
RouterOS CLI Command:
[admin@MikroTik] > /certificate add name=CLIENT1 copy-from="CLIENT-tpl" common-name="CLIENT1"
Now save it and sign it with the CA you’ve created.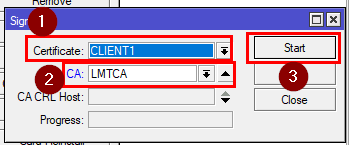
RouterOS CLI Command:
[admin@MikroTik] > /certificate sign CLIENT1 ca="LMTCA"
In the end, the certificate flags should be:
K, L, A, T - for the Certificate Authority
K, I, T - for the OpenVPN Server Certificate
K, I - for the Client certificates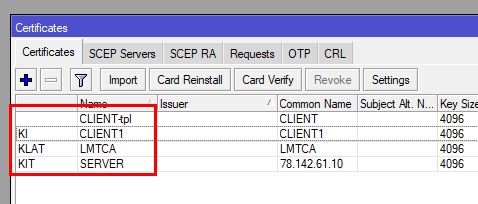
7d. Exporting and Downloading the certificates
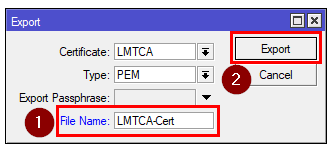
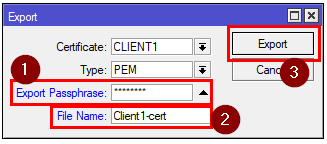
This is done by right-clicking them and selecting export. When you export the client certificate, make sure that you export it with a password.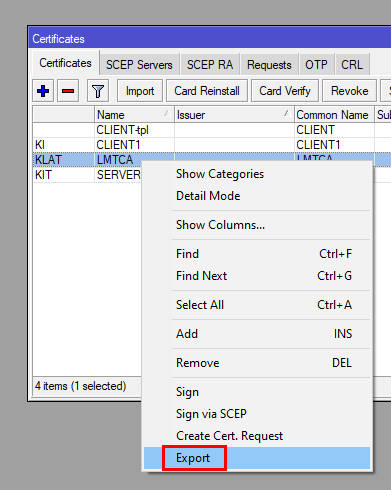
RouterOS CLI Command:
[admin@MikroTik] > /certificate export-certificate LMTCA export-passphrase=""
[admin@MikroTik] > /certificate export-certificate CLIENT1 export-passphrase=12345678
After you export them, you can easily download them using WinBox or other file transfer programs like WINSCP(via FTP/SFTP).
For WinBox, go to Files to locate your certificate files.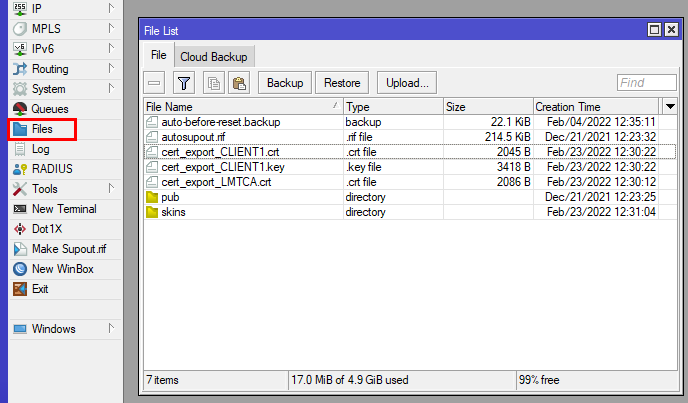
Then download them by dragging them into a folder on your computer.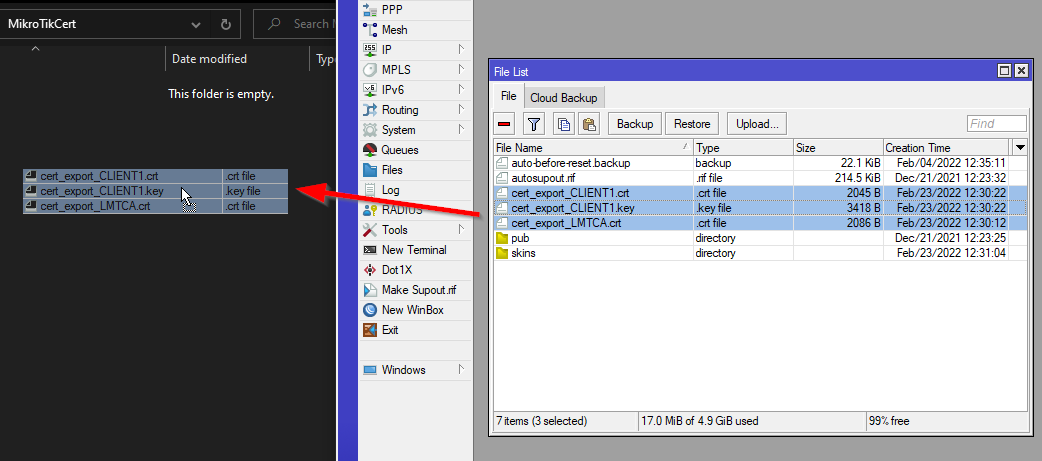
8. Enabling the OVPN Server
Go to PPP, click on “OVPN Server”, Check "Enabled", and set:
Port: 1194(or 443)
Certificate: SERVER
Require Client Certificate: true
Auth: sha1, md5
Cipher: Blowfish 128, aes 128, aes 192, aes 256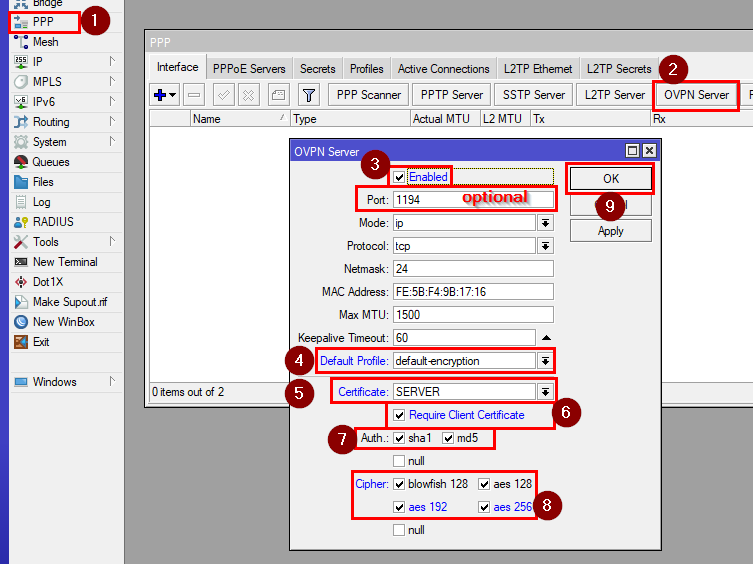
RouterOS CLI Command:
[admin@MikroTik] > /interface ovpn-server server set default-profile=default-encryption certificate=SERVER require-client-certificate=yes auth=sha1,md5 cipher=aes128,aes192,aes256,blowfish128 enabled=yes
9. Editing the default-encryption PPP profile
Go to Profiles, double-click the default-encryption profile, and set:
Local IP address: 192.168.34.1
Remote IP address: OVPN-pool
DNS servers: (e.g. Quad9) 9.9.9.9 and 149.112.112.112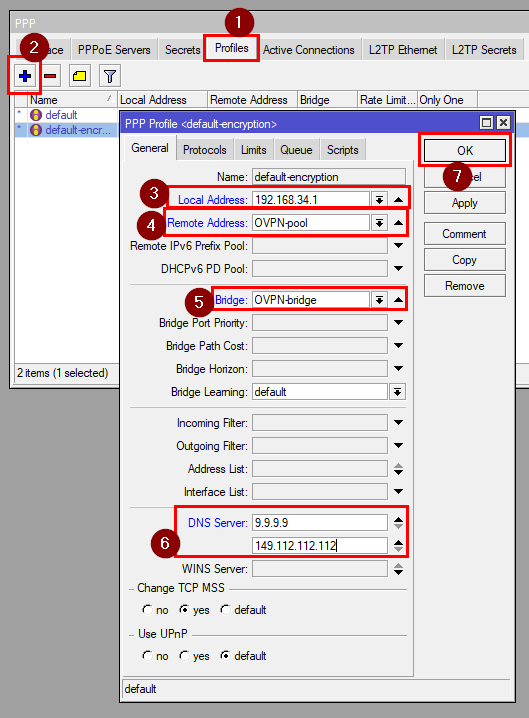
RouterOS CLI Command:
[admin@MikroTik] > ppp profile set default-encryption local-address=192.168.34.1 remote-address= OVPN-pool dns-server=9.9.9.9,149.112.112.112 bridge=OVPN-bridge
10. Creating a PPP account for the OpenVPN network
Click on the "Secrets" tab and then on "+". Set with credentials of your choice and select the default-encryption profile.
RouterOS CLI Command:
[admin@MikroTik] > ppp secret add name=BGOCloud-OVPN password=bgocloud profile=default-encryption comment="our first account"
And that's it. You've created an OpenVPN Server on your MikroTik Cloud Hosted Router, ready to accept OVPN connections.
You can now connect some devices to your OpenVPN network, using these tutorials:
Set up OpenVPN Client in Windows and Mac
Set up OpenVPN Client in Android
Set up OpenVPN Client in iPhone iOS
Take a look at our powerful MikroTik VPS servers and choose a suitable plan to get started.
If setting up this server is hard for you, you can take a look at our fast and secure OpenVPN Hosting plans. Easier and quicker to set up, more secure and it's ready in 5 minutes.

