How-To: Configuring WireGuard in MikroTik CHR - Faster and secure VPN protocol

WireGuard is a new and actively developed VPN protocol. It provides more advantages over the other VPN protocols, such as:
- Quicker connections and higher speeds.
- Easier and quicker to set up in a CHR instance.
No need to set up IP pools, VPN profiles and secrets. - Better traffic encryption.
Uses the newest state-of-the-art algorithms, such as Curve25519 for key exchange and ChaCha20 for traffic encryption. Resistant to decoding with quantum computers. - Better security.
You will not need a username and password for authentication, everything is done with keys. - No need for SSL certificates,
unlike in OpenVPN and SSTP. This means that is faster to be rebuilt. - Cross platform
supports Windows, MacOS, Android, iOS, Linux and other platforms. - Harder to block,
unlike PPTP and L2TP. Every time a different port is used, it is NAT and firewall friendly. - Less connection interruptions
unlike L2TP. - Less energy and computional power used,
compared to other VPN protocols.
Our Cloud Hosted Routers support this protocol beginning RouterOS v7. In this tutorial we will show you how to make your own Wireguard VPN server in your MikroTik CHR using WinBox, WebFig and SSH.
In this tutorial we will need:
- A CHR or other MikroTik Device that support x86/ARM CPU. You can check our plans and get a CHR here: https://www.bgocloud.com/hosting/mikrotik-vps
- A private network in the CHR, that will be used by the WireGuard interface and peers
- Some devices to connect to the WireGuard VPN Server
1. Updating the CHR
To use the latest Wireguard functions of RouterOS, we will first need to update our CHR to RouterOS v7, this is done easily from System>Packages and clicking on “Check for updates”.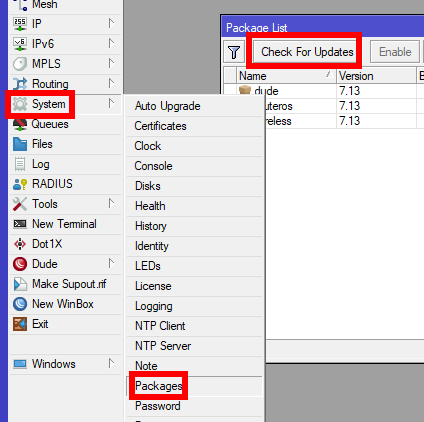
From there download the update if available and install it. If you use RouterOS v6, then change the channel to “Upgrade” to get RouterOS v7.
[admin@MikroTik] > system package update check-for-updates
[admin@MikroTik] > system package update download
[admin@MikroTik] > system reboot
2. Setting up the interface
To setup the interface, go to Wireguard and click on “+”. Then you can name it as you like and choose any port (except the service ones). To save it, click on OK. If you plan to use more than one Wireguard you can put a comment on them as well.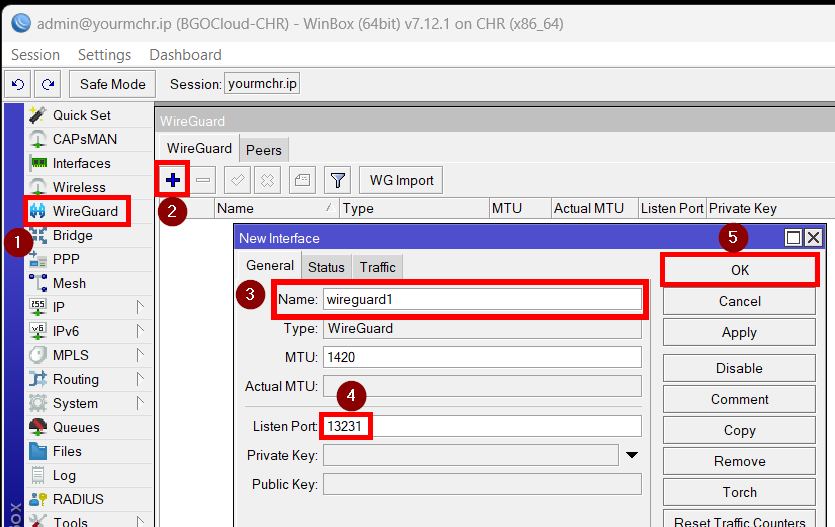
[admin@MikroTik] > interface wireguard add listen-port=13231 name=wireguard1
After that we need to set an IP address of the Wireguard interface. To do that, go to IP>Addresses, click on “+”. Select any private IP address and choose the Wireguard interface you have created. In our example we will use 192.168.34.1/24. Please note that to make a Wireguard network, it is best to choose the first usable IP address of a private IP network. We will later manually assign the other IP addresses to our clients, also called peers, later in the tutorials.
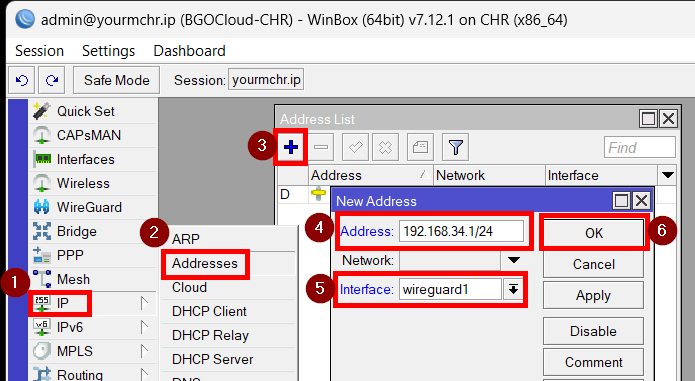
[admin@MikroTik] > ip address add address=192.168.34.1 interface=wireguard1
3. Setting up the firewall for Wireguard.
Now we will need to set up the firewall. If you have a restrictive firewall or a firewall like in our Security basics article then we need to add a rule for the Wireguard port to ensure seamless connections. For that go to IP>Firewall, click on "+" and then enter the following:
Chain: input
Protocol: UDP
Destination port: the listening port that you have set in the second step, default 13231
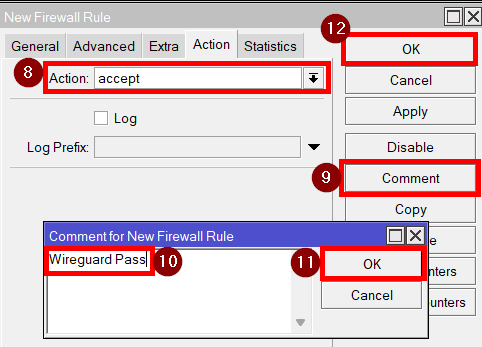
Action: accept
You can comment on the rule by clicking on “comment” and enter “Wireguard pass”. That way we know that this rule is for establishing Wireguard connections. Click on “OK” to save the rule.
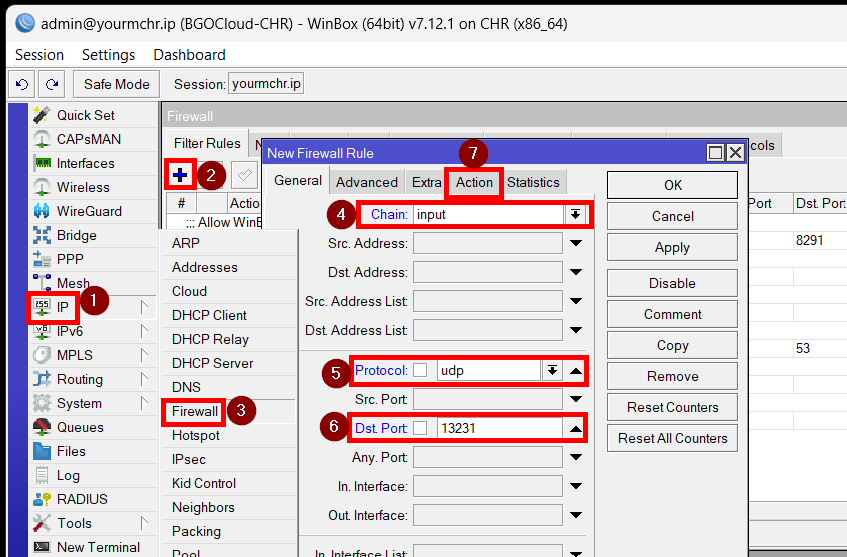
Then simply drag the rule above the drop rules, you can even put it to the top.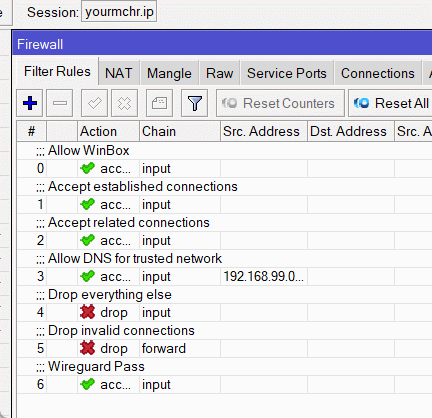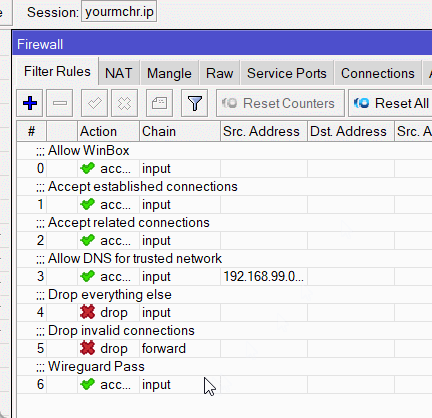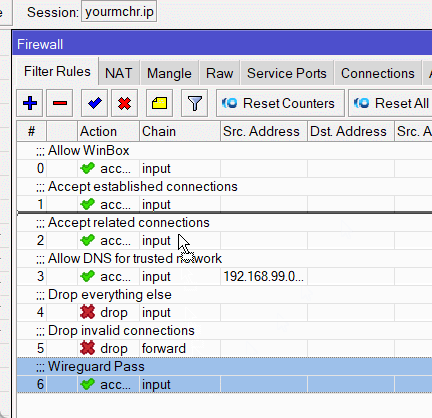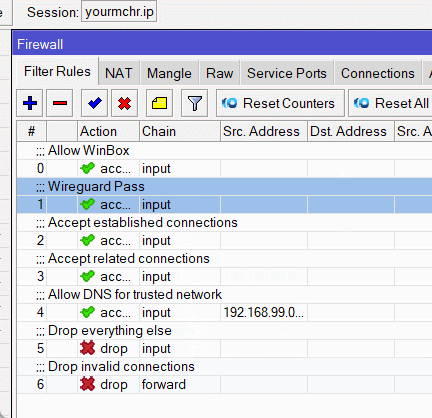
For RouterOS CLI you can use the command below, change the port, according to your configuration.
[admin@MikroTik] > ip firewall filter add chain=input action=accept comment="Wireguard pass" protocol=udp dst-port=13231 place-before=1
After that go to the NAT tab and add a masquerade rule to allow access to the internet for your Wireguard network.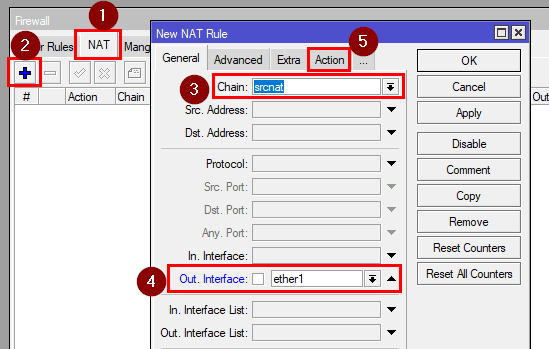
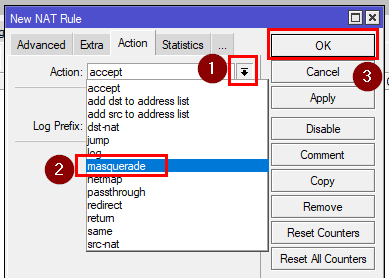
[admin@MikroTik] > ip firewall nat add chain=srcnat out-interface=ether1 action=masquerade
4. Additional firewall configuration for using internal or Pi-Hole DNS
If you plan to use the CHR as the DNS server, or you run an internal DNS from a container, for example a Pi-Hole DNS made in another of our articles, then you need to add some additional rules to your firewall.
These rules allow the devices on your WireGuard network to access other services on your CHR, other than the publicly available ones.
Create a new rule by clicking on "+" and enter the following:
Chain: input
Src. Address: The WireGuard network, in our example - 192.168.34.0/24
Action: accept
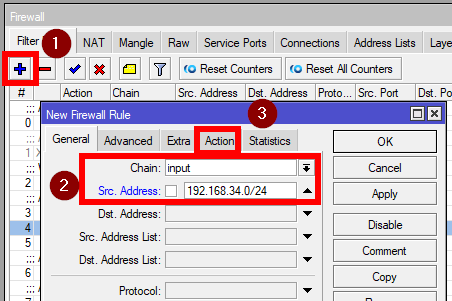
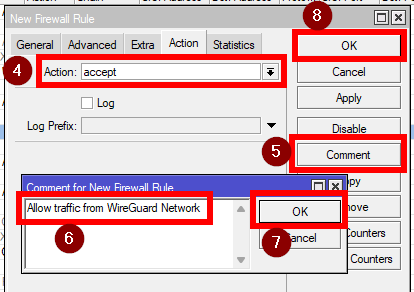
Then simply drag that rule above the drop rules as well.
For RouterOS CLI you can use the command below, change the source address, according to your configuration.
[admin@MikroTik] > ip firewall filter add chain=input action=accept src-address=192.168.34.0/24 comment="Allow access from WireGuard network" place-before=1
We are done configuring the Wireguard interface. Now we need to add some devices that will use your newly created Wireguard server.
You can check our other tutorials on connecting devices to your newly created Wireguard VPN:
Connecting computers to the WireGuard VPN
Connecting Android and iPhones to the WireGuard VPN server
You can also check our powerful MikroTik CHR plans and choose a suitable plan to get started.

